The SixMap Computational Mapping Platform
Start with Enterprise Name Only
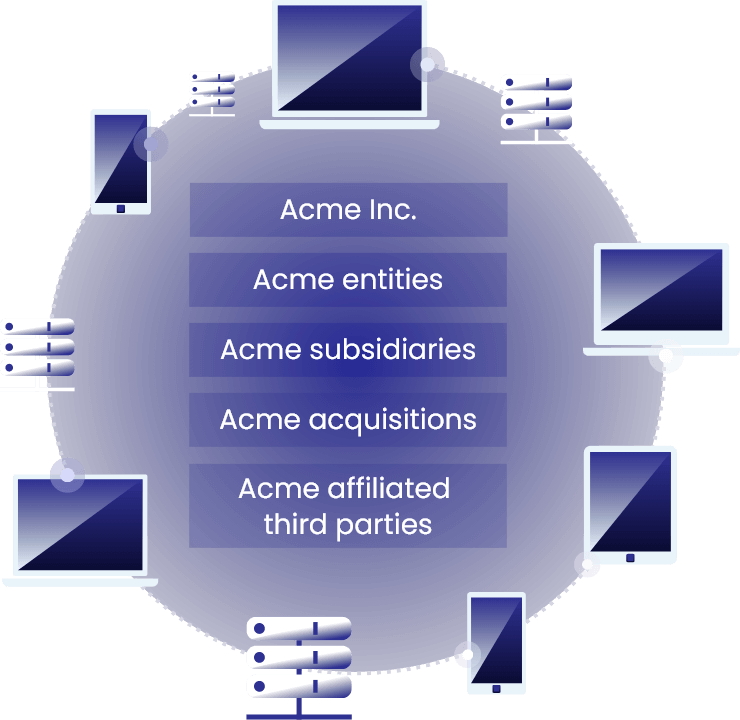
All you have to do is provide your enterprise name to SixMap.
Thanks to SixMap’s zero-touch architecture, there is nothing to install, and no access, or privileges needed.
SixMap generates a list of the extended enterprise including entities, subsidiaries, acquisitions, and affiliated third parties, across all locations.
The power SixMap provides is the organizational context to really understand what you’re defending. Traditionally achieved through spreadsheets, emails, and coordination across departments, SixMap automates this process, generating all necessary data to map the extended enterprise.
Comprehensive Enterprise, Network, and Vulnerability Discovery
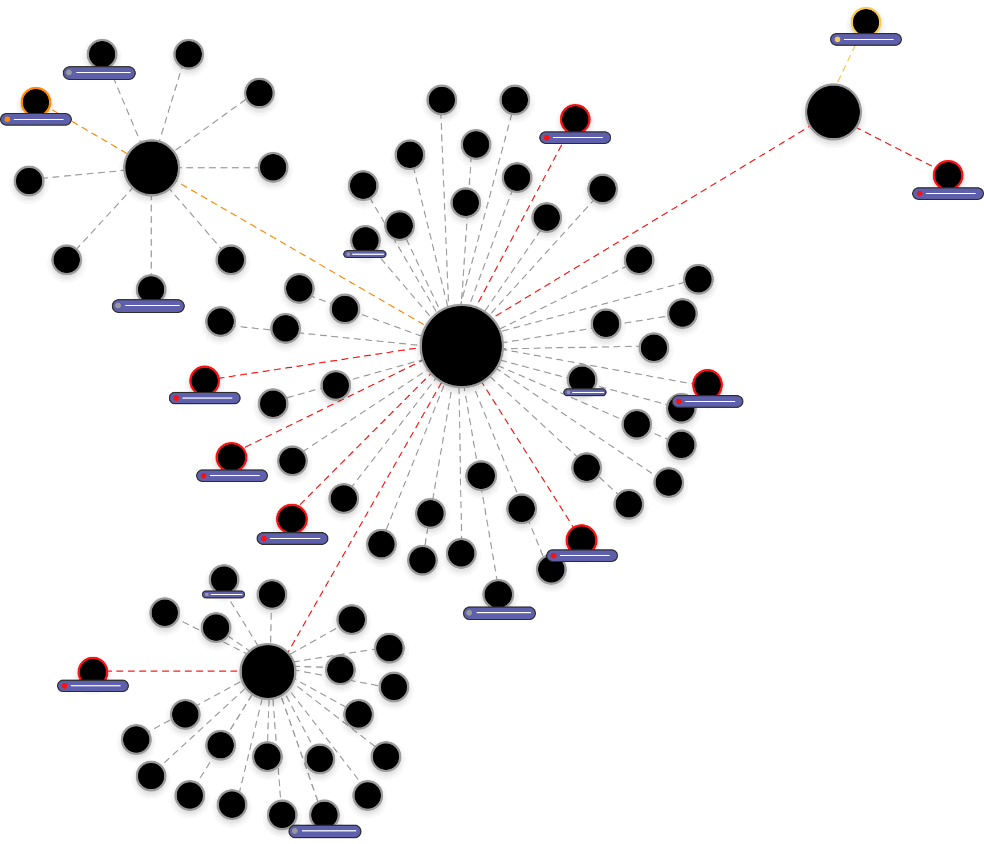
From there, SixMap automatically discovers every Internet-connected asset and device associated with the enterprise, enumerating services across all 65,535 ports on all IP ranges.
SixMap then re-interacts with all open ports to discover vulnerabilities even if the exact service is not known, such as navigating to specific web pages on a web server. This highly interactive process enables SixMap to discover vulnerabilities that cannot be detected with service detection nor banner grabbing alone.
The result is comprehensive visibility of your enterprise, Internet facing services, devices, as well as vulnerabilities and misconfigurations across your extended enterprise. But we don’t stop there.
Contextual Exposure, Exploit, and Threat Intelligence
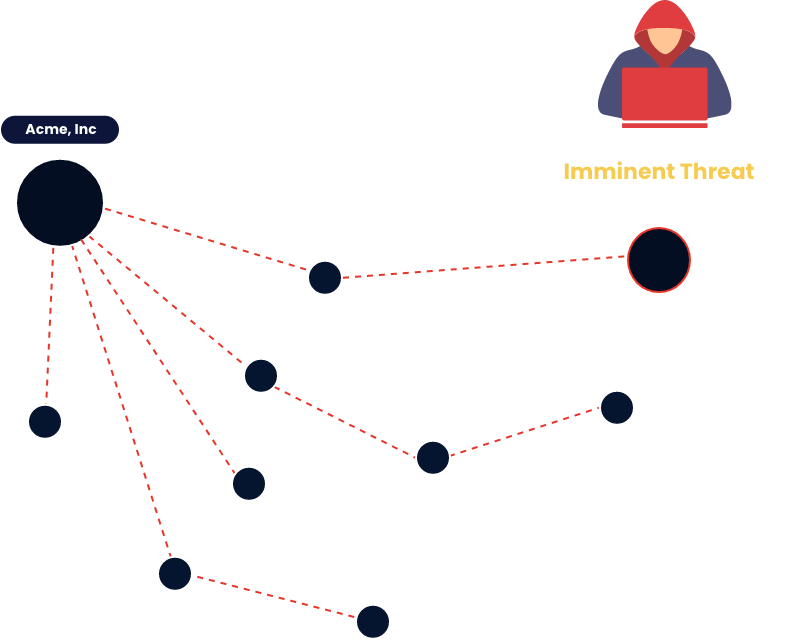
SixMap maintains near real-time global threat intelligence about threat actor activity everywhere on Earth, including who they are, what they do, and how they do it.
SixMap fuses this global threat information with the comprehensive picture of your environment to identify imminent threats to your enterprise.
This imminent threat information includes a specific threat actor, which exploit they will use, and which customer network, device, and vulnerability they will exploit.
Automated Remediation and Validation
Once SixMap identifies a specific imminent threat, the information is delivered to your SOC via API. In addition, SixMap generates solutions to stop the threat.
SixMap can validate exploitability before a fix is deployed and validate remediations to ensure that the fix was implemented properly.
SixMap is also the only platform that can auto-fix vulnerabilities remotely with no action required from the customer. While this step is entirely optional, we have demonstrated it is indispensable when defending large enterprise during ferocious, high speed attacks.
See the SixMap Platform in Action
To see a demo with your company’s actual data, schedule a time to talk with us today.

