The recent cyber attack against Change Healthcare sent shockwaves throughout the U.S. healthcare sector. More than 100 applications across pharmacy, medical record, patient engagement, and payment services were affected. The attack has impacted millions of lives, causing loss of reputation, market capitalization, and UnitedHealth Group has already paid out more than $3.3B to providers affected by the cyberattack. This incident not only highlights the sophistication of modern cyber threats, but also serves as a case study in the rapid evolution of cyberattack methodologies towards speed.
In this blog post from the SixMap Research Team — with commentary from former healthcare Chief Information Security Officers and National Security Agency leadership — we argue that the speed of the attack leveraging the ConnectWise vulnerability, and the speed of other similar breaches, requires organizations to take steps towards a fully automated approach to network and cyber defense.
The complexity of defending today’s highly dynamic and multifaceted enterprise networks combined with the speed that adversaries exploit vulnerabilities unsurprisingly continues to result in organizations with established cyber security programs falling victim to breaches. We break down our discussion of a solution leveraging automated cyber defense into three distinct components: 1) continuous global threat intelligence mapping, 2) continuous monitoring and vulnerability mapping, and 3) automated defense capabilities.
The Anatomy of the Attack
Attributed to the notorious ALPHV/BlackCat ransomware group, the Change Healthcare attack was not just a standard ransomware encryption operation but a more sophisticated campaign that leveraged a combination of encryption and data exfiltration. This attack underlines a chilling evolution in cyber threats: a hybrid approach that not only seeks to paralyze operations through encryption but also to create lingering threats through the extraction of sensitive data.
Although UnitedHealth Group (UHG) has not publicly disclosed the initial attack vector, SixMap has been tracking two specific vulnerabilities thought to be pivotal in this attack, CVE-2024-1708 (identifies a vulnerability in ScreenConnect) and CVE-2024-1709 (identifies a known exploited vulnerability also in ConnectWise ScreenConnect) since mid February. These vulnerabilities allow adversaries to create administrative users on a ScreenConnect server and enable remote code execution with administrative privileges, essentially handing over the keys to the kingdom.
There is still a lot of speculation on the exact nature of the exploit used by ALPHV/BlackCat and affiliates and their association with the Change Healthcare hack and ConnectWise vulnerabilities. ConnectWise maintains that it “is unaware of any confirmed connection between the ScreenConnect vulnerability disclosed on February 19th, 2024, and the incident at Change Healthcare.” Change Healthcare submitted their 8K SEC filing early this month, without any further insight into the exact causes of the breach.
Technical Insights and Cybersecurity Implications
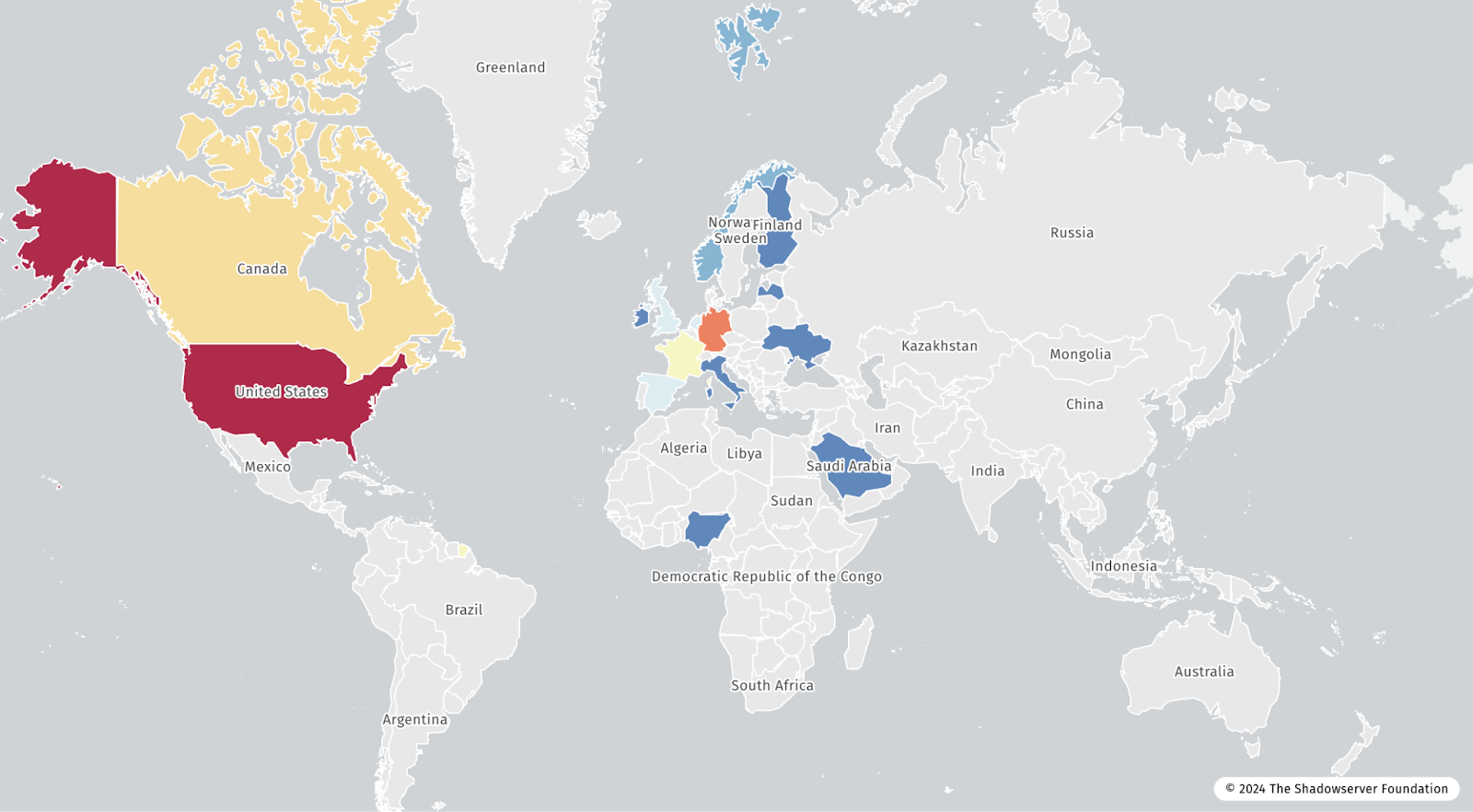
Despite the controversy surrounding the attacks, what is certain is that it was pervasive, as evidenced by data from ShadowServer shared in Figure 1 that shows honeypots exploited via CVE-2024-1709 across every populated continent. Threat actors were quick to exploit this vulnerability making this exploitation one of the fastest moving in 2024. We observed just four days between disclosure by the vendor and massive scale exploitation in the wild. SixMap global threat intelligence observed the disclosure on 19 Feb 2024, exploit code released for CVE-2024-1709 on 21 Feb 2024, and exploitation in the wild by adversaries on 22 Feb 2024.
The fact that these vulnerabilities were exploited at scale mere days from disclosure underscores a critical gap in the current cybersecurity posture of many organizations: the speed of response. The attack velocity from vulnerability disclosure to exploitation on a massive scale illustrates the need for an agile approach to cybersecurity.
Continuous Global Threat Intelligence Mapping
It is possible to proactively prevent a cyber attack, if you have timely and accurate threat intelligence that the attack is coming. Conversely, without comprehensive threat intelligence it is intractable to respond to all imminent threats.
Intelligence should be mapped to the customer’s network and systems, enabling defenders to take action against only those threats to which they are vulnerable. In addition, analysis should enable defenders to identify the “blast radius” of a breach. This threat context empowers defenders to take time-sensitive action and stop attacks before they happen. It is also important to automate threat intelligence collection and contextual analysis, threat intelligence processing is often manual with delayed, limited, and non-specific intelligence.
Within just a few days of vulnerability disclosure, SixMap observed exploitation activity in the wild, and global exploitation every day for the next week. This strong “attack signal” expedited remediation and response for customers with these vulnerabilities exposed.
Rob Joyce, the former director of the National Security Agency’s Cybersecurity Directorate shared that, “threat intelligence provides guideposts to discovering past exploitation and gives you the advantage of knowing where to look when defending into the future. Empirical data allows the best use of finite defensive capacity and expertise.”
Continuous Monitoring and Vulnerability Mapping
At SixMap we often say, “you cannot defend what you cannot see.” The ability to instantly see all of the systems that have a specific vulnerability is the first step in responding to an imminent threat of cyber attack. Both of the vulnerabilities leveraged in the attack could be quickly mapped back to network assets via a specific service version number if the customer had a near real time inventory of all exposed network services and version numbers.
However, we argue customers should also leverage capabilities that interact with exposed services to go beyond version number identification and validate exploitability because in many cases a vulnerability can only be exploited if a particular feature is enabled for a particular service version number. This deep interrogation is especially important for HTTP based services, which was the protocol used for this attack, because version detection alone introduces 1) false negatives where it is not able to detect specific vulnerabilities that are not based on the server version or 2) false positives because specific configurations of the web server (despite having the vulnerable service version number) are required in order to be vulnerable, see CVE-2021-40438.
Organizations need vulnerability detection capabilities that continuously perform asset inventory, identify service and version numbers, and check configuration settings via interactive service interrogation, so that defenders have accurate empirical “ground truth” data required to quickly and efficiently identify exactly where they are vulnerable in response to threats.
Automated Defense Capabilities
The case for automated defense in cyber is compellingly illustrated by the potential for immediate remediation of vulnerabilities when faced with a fast moving imminent threat. Organizations should deploy capabilities that give them the option, but not the obligation, to auto-fix vulnerabilities at scale. When defenders are dealing with fast moving attacks that allow adversaries root privileged remote code execution, automated remediation should be available as an option to stop the attack.
It was possible for SixMap to auto-fix the vulnerabilities used in this attack, remotely over the Internet, with zero touch, and no agents — in just a few minutes, even for Fortune 500 customers with global networks. This was possible because SixMap automatically leveraged the vulnerabilities to obtain privileged execution on the application and then downloaded and installed the patched version of ScreenConnect to fix the vulnerability. While this process did wipe the existing user database on the ScreenConnect server, only users with local accounts required a new username and password to access ScreenConnect; users connecting via Active Directory or an Identity Provider (idP) were able to access ScreenConnect at their next login. To resolve the local account, SixMap securely sends a new local admin account username and password to the customers’ security operations center, so they can immediately reset it. Although SixMap has the capability to provide this service to customers, it will only be done with the customers explicit permission in advance. SixMap never takes unauthorized actions against customer infrastructure without explicit approval in advance.
We believe that the risks from this automated remediation approach were substantially smaller than the risks posed by the imminent threat of this specific cyber attack. However, SixMap always offers customers a choice in the form of a phased approach to automation.
The journey toward effective cyber defense often begins with enhancing visibility and responsiveness to imminent threats. This initial step involves near real-time monitoring and alerting systems that provide actionable insights, including recommended remediation steps for security teams to implement. Such capabilities are fundamental in equipping Security Operations Centers (SOCs) with the tools needed to address vulnerabilities promptly.
As organizations evolve in their cybersecurity maturity, the decision to incorporate varying levels of automation becomes crucial. This progression allows for a tailored approach, enabling actions based on predefined conditions. Looking ahead, the future of cybersecurity lies in the potential for fully automated remediation processes. This advancement promises a significant leap forward in defense capabilities, particularly in scenarios where rapid response is critical.
Our auto-fix capabilities are currently available for alpha testing and we are developing a framework where automated defenses activate only in the most acute situations with prior customer approval. This includes situations when the vulnerability enables remote code execution with administrator or root privileges and we observe a fast moving imminent threat of exploitation to our customers according to our global threat intelligence.
That was certainly the situation in this case, and we believe that the speed of this attack demanded a fully automated response. As attackers move faster and attacks become more automated, it will become important for more customers to consider leveraging fully automated cyber defense.
Jim Routh, the former CISO/CSO of Aetna, MassMutual, and CVS Health shared that, “driving risk management workflow/transactions without dependence on humans is what cyberleaders need. This approach delivers real-time risk management protection without a dependence on humans to process information/transactions. It is more effective with lower operating costs, increasing capacity to drive business growth.”
Toward a More Resilient Future
The ConnectWise vulnerability serves as a potent reminder of the ever-evolving landscape of cyber threats. As attacks increase in ferocity, speed, and number, people need to leverage automation as a force multiplier; for cybersecurity professionals, it’s a call to arms to embrace automated tools and methodologies. Defenders need an advanced warning and control system for automated response – similar to “over the horizon” Airborne Early Warning & Control (AWAC) Platforms – to detect, track, prioritize, and stop attacks before they strike.
Within minutes of adversaries exploiting the vulnerabilities used in this attack (anywhere on earth), automated cyber defense solutions such as SixMap could provide a platform providing customers with the utmost flexibility in establishing automation as part of their defensive operations to auto-fix these vulnerabilities and defend global enterprise customers from this incoming attack “just in time”.
Omar Khawaja, the former CISO of Highmark Health shared that, “the urgency for automated cyber defense is clear. As the gap between vulnerability disclosure and widespread exploitation narrows, the need for auto-fix shifts from optional to essential. Empirical data about the threat empowers organizations to act proactively. Traditional methods fall short; it’s essential for CISOs to begin transitioning to automated defenses.”



