Gain complete and accurate data on your assets, exposures, and risks.
The SixMap Solution

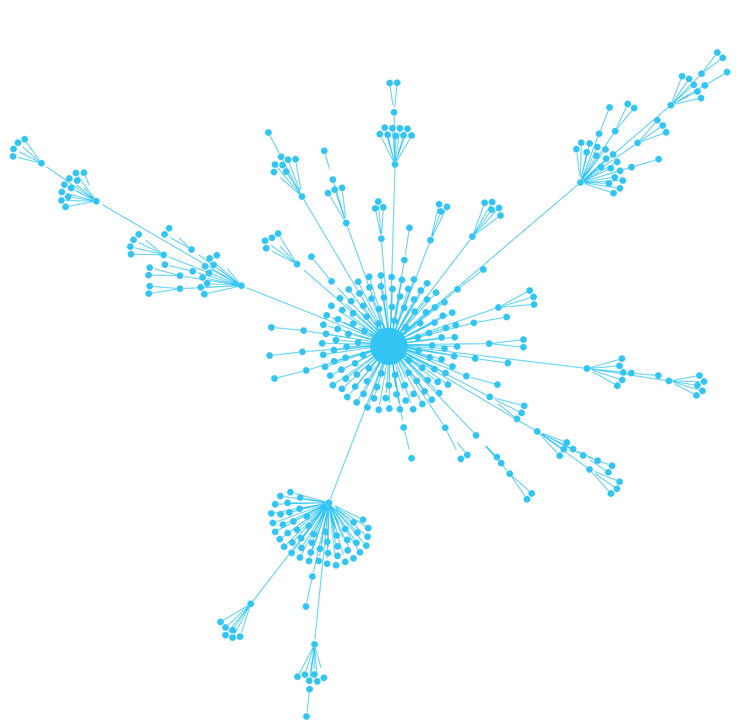
Step 1: Organizational Mapping
The only thing needed to get started is an organization’s name.
From there, SixMap creates a map of the corporate structure, identifying all subsidiaries and legal entities globally.
The organization map provides two main benefits:
- First, every entity acts as an initial starting point for the host discovery procedure, leading to a much more robust asset inventory.
- Second, all discovered assets are automatically categorized by the legal entity to which they belong, resulting in data that’s more structured and much easier to manage.
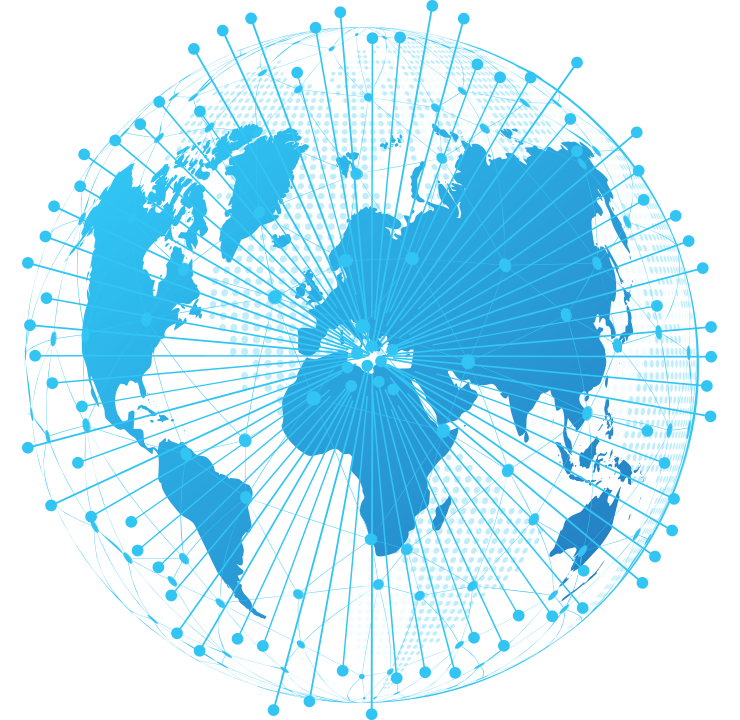
Step 2: Host Discovery Across IPv4 & IPv6
The cornerstone of the SixMap platform is an innovation called 6Gen.
6Gen discovers hosts across both IPv4 and IPv6 with extremely high precision, providing far more complete data than legacy techniques that rely exclusively on WHOIS and DNS records.
Why IPv6 discovery is critical:
- Many security leaders wrongly assume their organization isn’t using IPv6.
- We routinely find IPv6 addresses in use for almost every large organization we evaluate.
- Internal research shows that 6% to 9% of an enterprise’s IP addresses are in the IPv6 space, leaving many assets unmonitored.
Step 3: Comprehensive Exposure Assessment
SixMap’s exposure assessment process inspects all 65,535 ports on each host.
Our platform autonomously finds which ports are open and identifies the service and version number in use.
Why SixMap outperforms legacy tools:
- Legacy exposure assessment tools only scan the top 1,000 to top 5,000 most commonly used ports, but this leaves many exposures undetected.
- Research shows that roughly 7% of services run on non-standard ports that fall outside the top 1,000.
- Any tools that fail to inspect all ports are creating potential blindspots and hidden risks.
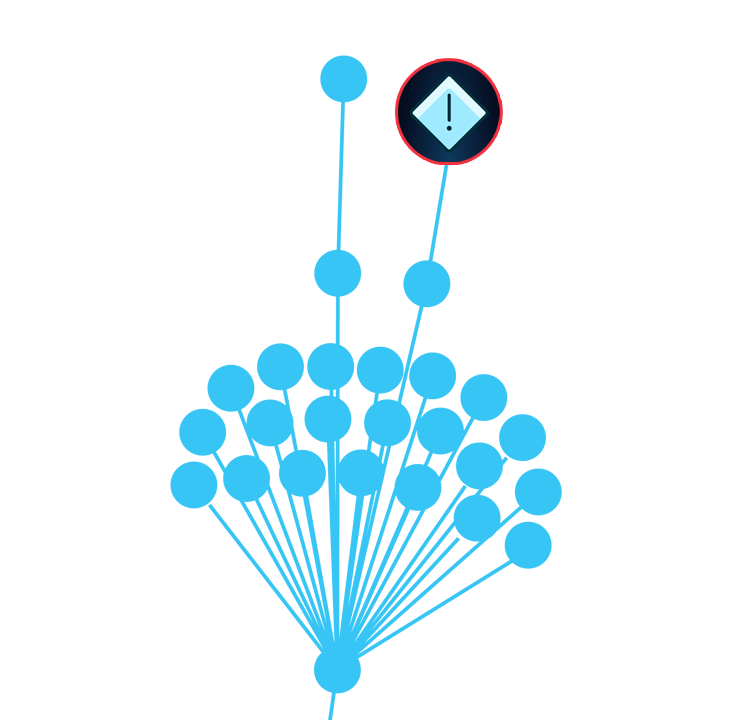
Step 4: Prioritization Using Threat Intel Data
Our solution detects CVEs and enriches each one with threat intelligence data.
This automated prioritization process factors in the severity of the vulnerability, whether or not it’s known to be exploited in the wild, the probability it will be exploited within the next 30 days, and which threat groups are known to exploit it.
Why enrichment matters:
- SixMap reduces friction in security operations and vulnerability management.
- Security teams can focus efforts on the real risks that matter most.
- Time is used efficiently and critical risks are mitigated before an attack occurs.
See the SixMap Platform in Action
Schedule time with us to see a customized demo tailored to your organization’s data.
Download the Solution Brief
to learn more.
At its core, exposure management is a data problem. With perfect data, security teams would know exactly what risks exist and which need to be mitigated first. Unfortunately, legacy tools provide data that’s both incomplete and inaccurate.
SixMap brings new innovations to market to address these familiar challenges. Read the SixMap Solution Brief to understand the business value of comprehensive and precise exposure data.


